ATT&CKing Threat Management
It would be really awesome to map out the most common techniques used by threat actors and prioritize those for detection, right? It would also be really awesome to know what our defense-in-depth capability looks like for the enterprise compared against threat actor techniques. Woah, slam those together and you start to get a picture of true threat-informed defense. I actually proposed something exactly like this in my SANS Research Paper, “ATT&CKing Threat Management: A Structured Methodology for Cyber Threat Analysis”. Academic papers aren’t the funnest things to read, so here’s the TL;DR version.
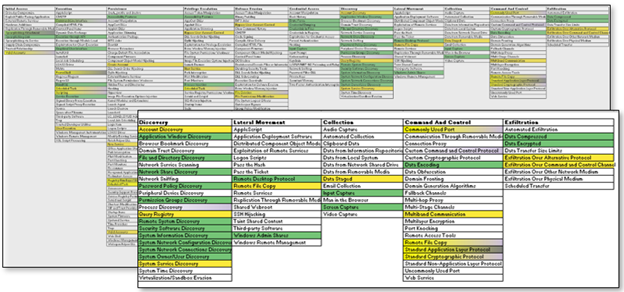
Here are the top techniques found in the 50 reports that I processed for my research paper. I plan to continue to catalog threat reporting and possibly put out an annual Top Ten list. More on the research approach below…
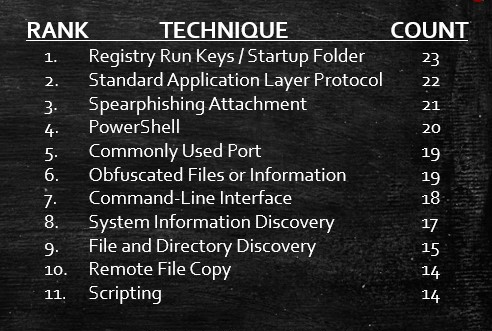
The Concept:
Basically, my research aimed to process a bunch of threat reporting and catalog them using the MITRE ATT&CK framework to identify trends, build a prioritized list of techniques for defenders, and identify any other cool analytics I could pull out of the dataset. I used this structured approach:
- Collect — publicly available threat reporting that discusses specific threat activity
- Catalog — threat reporting into Airtable using the ATT&CK techniques as multi-select values
- Assess — the trends in the ATT&CK techniques observed across the body of reporting
- Act — by informing resource management prioritization
The Academic Thesis:
By leveraging the MITRE Adversarial Tactics Techniques & Common Knowledge (ATT&CK) framework as a quantitative data model, analysts can bridge the gap between strategic, operational, and tactical intelligence while advising their leadership on how to prioritize computer network defense, incident response, and threat hunting efforts to maximize resources while addressing priority threats.
The WHY:
Organizations have limited resources and a world of threats to assess and prioritize. Without effective threat management prioritization, organizations:
- Cannot protect against the most likely threat vectors and actors
- Cannot implement an informed defense-in-depth (DiD) strategy
So how do we definitively answer questions like:
- What are the latest threat actor techniques?
- What logs should we collect?
- What hunts should we prioritize?
The HOW:
For my database, I ended up using the free version of AirTable and it was super easy to set up. Here is the database structure I used. As noted in the final section of this post, future-me would just put all techniques into a single dropdown column to make searching for them faster.
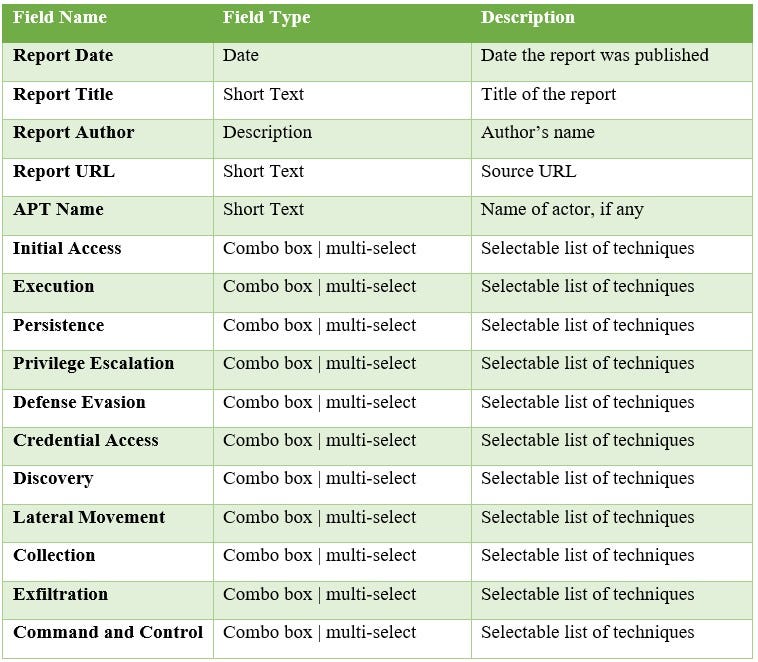
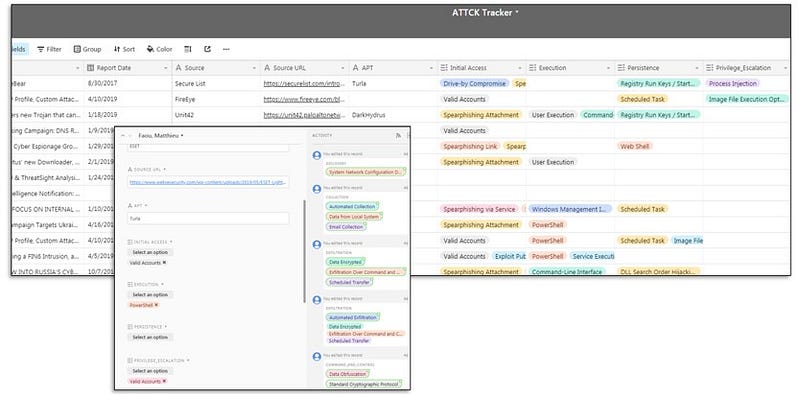
So I read a bunch of reports, inputted them into this database, and cataloged them using the ATT&CK techniques I was able to translate out of the text. So a threat report says something like “System Enumeration” and that can translate to “System Information Discovery” (T1082). The below image shows how I extracted the techniques from the NCCIC report TA17–117A into the ATT&CK Tracker.
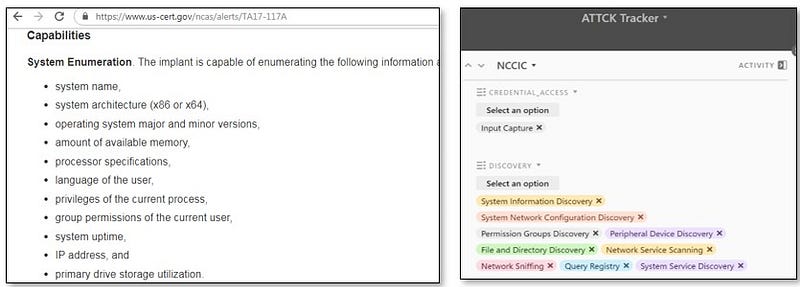
I repeated that process across 50 different reports and various source types to populate my ATT&CK Tracker, which is shown below. AirTable makes it really easy to go from the spreadsheet view to an input form view by simply click on the first cell in the record. As an MS Access addict, I have to say I love AirTable a bit more for its simplicity.
Now’s a good point in the article to toss out a HUGE SHOUT OUT to the analysts and vendors that are including ATT&CK tables at the bottom of their reports. I started referring to these tables as the “executive summary for threat analysts” since they give you a very clear picture of what happened in an attack. For example, FireEye used ATT&CK in their Triton blog in 2019. (Miller, Brubaker, Zafra, & Caban, 2019). In highly dynamic environments, such as a SOC, the immediacy of this threat data in a table is instantly applicable to threat analysis procedures.
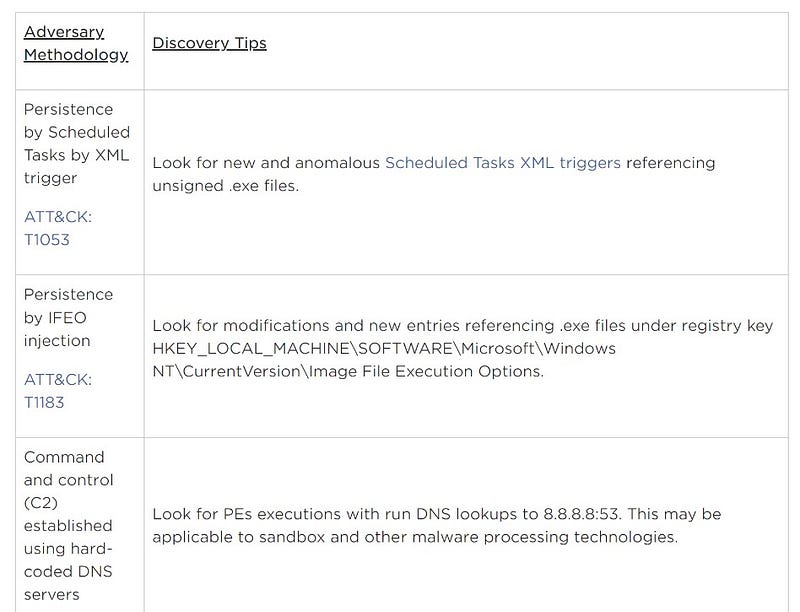
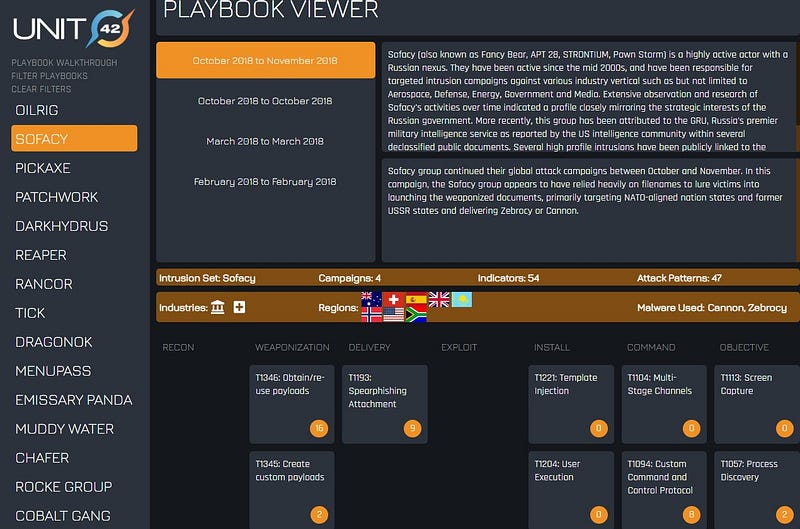
And FireEye isn’t the only vendor doing awesome stuff with ATT&CK and threat reports. The good folks at ESET map MITRE ATT&CK techniques to specific IOCs in their reports too. See their Winnti Group report for a specific example. One of my favorite MITRE ATT&CK tools for threat actor and campaign tracking is the Unit 42 Playbook Viewer. My only complaint is that they don’t source any of their analysis and IOCs on these pages.
Findings and Application
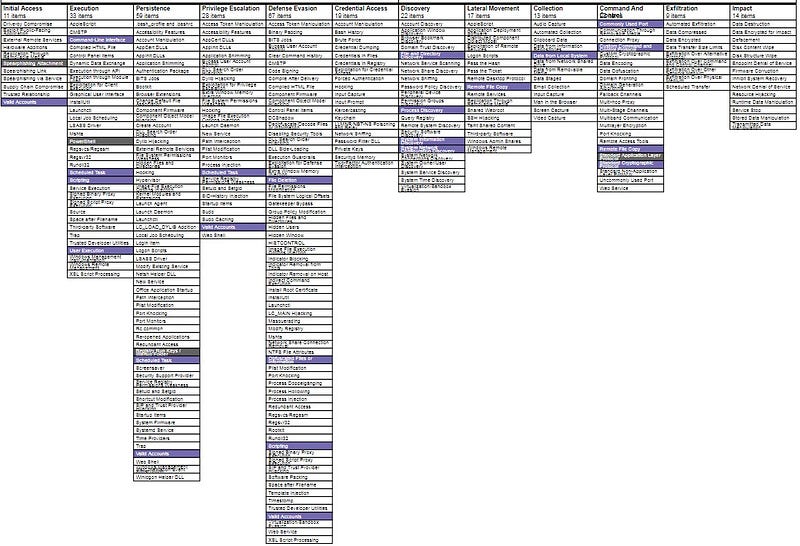
In the end, I processed 50 reports from 22 unique sources. There are 613 categorizations with 122 unique techniques. The reports span over 40 different threat actors. This is where things got real fancy. I exported the data from AirTable into the world’s greatest analyst tool, Excel, and ran some basic statistics against the data to identify the Top Ten observed techniques. Additionally, I used the MITRE ATT&CK Navigator to plot out the techniques that appeared in twenty or more documents as highlighted grey while those identified within ten to twenty reports were highlighted purple.
After analyzing the dataset a bit more, I created a defense-in-depth map using the ATT&CK Navigator for a make-believe company I called “Notional Inc.” For this scenario, I gave them a leading Endpoint Detection and Response (EDR) solution, an Intrusion Detection System (IDS), and an email security appliance. Collectively, this notional security stack provides monitoring coverage for the techniques highlighted in green. Yellow denotes where the existing tools provide enough visibility for threat hunting, but where the organization’s visibility is limited. For example, Notional Inc.’s IDS can monitor and alert on HTTP traffic, but it is blind to TLS traffic in this notional environment, so the C2 Tactics are labeled yellow.
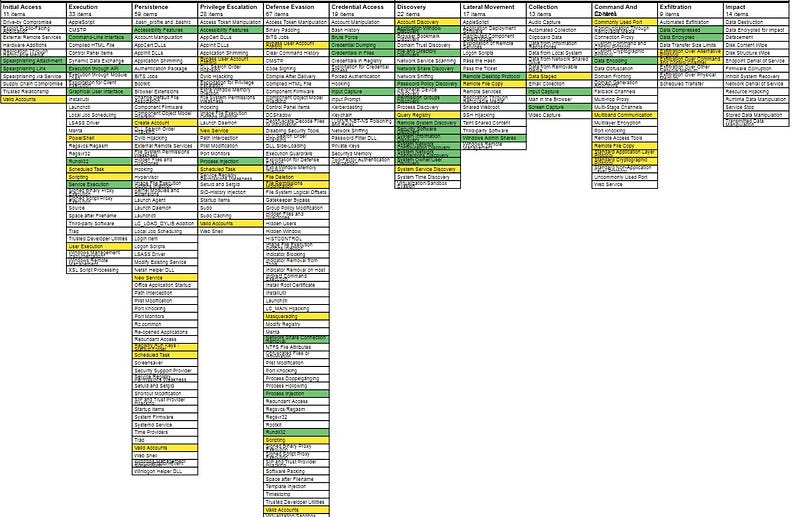
Once those two were created, it was logical to put them together to create a visualization of the gaps in coverage for Notional Inc. For example, this fictitious company currently does not have the detection capabilities for Process Discovery (T1057) and Custom Command and Control Protocol (T1094)
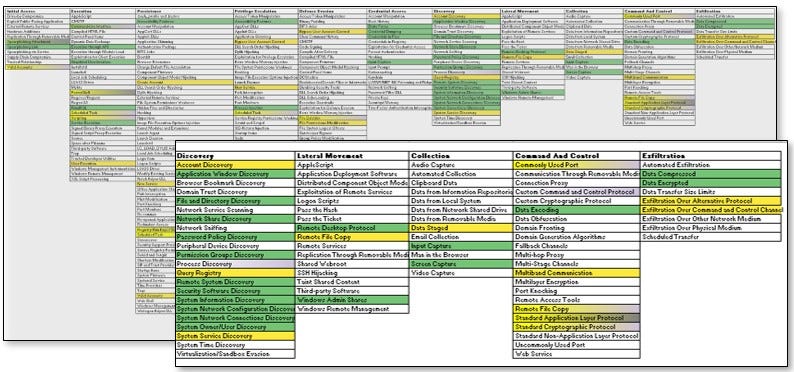
Just consider the idea of this dashboard on a SOC wall — one that actually shows the current state of defense coverage with an overlay for threat actor capabilities. Or imagine a threat actor briefing with the capabilities of a specific actor overlaid onto the defense-in-depth map. These could be powerful visuals for telling a story and driving change within an organization. It is worth noting, that I would use a slightly different color setup then the Green = monitoring coverage and yellow = some visibility. A better setup is Visibility + Monitoring = Green, Partial Visibility + Monitoring = Yellow, Limited Visibility = Red, no Visibility = Black. This color scheme married with a collection management framework would make the perfect cyber threat intelligence tools for an organization.
Lessons Learned and Future Implementations
Honestly this report and technique tracking should really be done in Threat Intelligence Platform (TIP) (for my thoughts on TIPs, check out my article “An Analyst’s Need for a Threat Intelligence Platform”. So far though, I’ve only seen most of the major TIP vendors using ATT&CK as a tag, which doesn’t really enable analytics and trending like I needed for this project. Also, most of the big-name TIPs generally don’t do analytics and trending very well, which is a huge oversight and a completely different rant… I know of one single analyst platform that does both really well. (Feel free to reach out if you’d like to know more about it.)
Anyway, here is a quick list of the lessons-learned, things I’d do differently, things I like to see done with future research, and other random thoughts:
- Using this technique with internal incident response data, sandbox reports, etc. would go a long way to making this extremely effective for prioritizing defense coverage
- In a TIP, I’d have all ATT&CK TTPs in a single dropdown field with multi-select enabled. This would save a lot of time of trying to find the correct Tactic field to find the corresponding Technique.
- Love to see more threat vendors include ATT&CK in IOC packages
- AirTable can convert existing values into multiple-choice options which can save hours during system creation
- DiD color scheme — Visibility + Monitoring = Green; Partial Visibility + Monitoring = Yellow; Limited Visibility = Red; no Visibility = Black
Oh… and I put all of this material into a set of slides. Enjoy!
[embed]https://www.slideshare.net/AndyPiazza/attcking-threat-management[/embed]
